Enter your email address to receive the latest ITVET news, market insights, and useful IT tips.
Ransomware is one of the most popular types of cyberattacks that uses social engineering techniques. In 2022, there were over 493 million ransomware attacks globally – that’s more than double pre-pandemic levels.
Ransomware threats are increasing across all industries, including property, retail, and hospitality. A new report warns that AI will cause a surge in both volume and impact of ransomware over the next few years.
Our Ransomware Guide covers all the essentials, including what it is, ransomware prevention methods and how to recover from an attack.
What is ransomware?
Ransomware is a type of malware (malicious software) that blocks access to your computer system or data until you pay a sum of money (ransom). If the ransom is not paid by a specified time, the data can be permanently lost or even leaked to the public. This can be catastrophic for companies that rely on the data to maintain business operations.
The average cost of a ransomware attack
The average cost of a ransomware attack stretches into the millions. The ransom itself can be substantial, and there are other costs to factor in, such as reputational damage and loss of business. In the UK, the average ransomware payment in 2023 was $2.1 million, which is higher than the global average.
How does ransomware work?
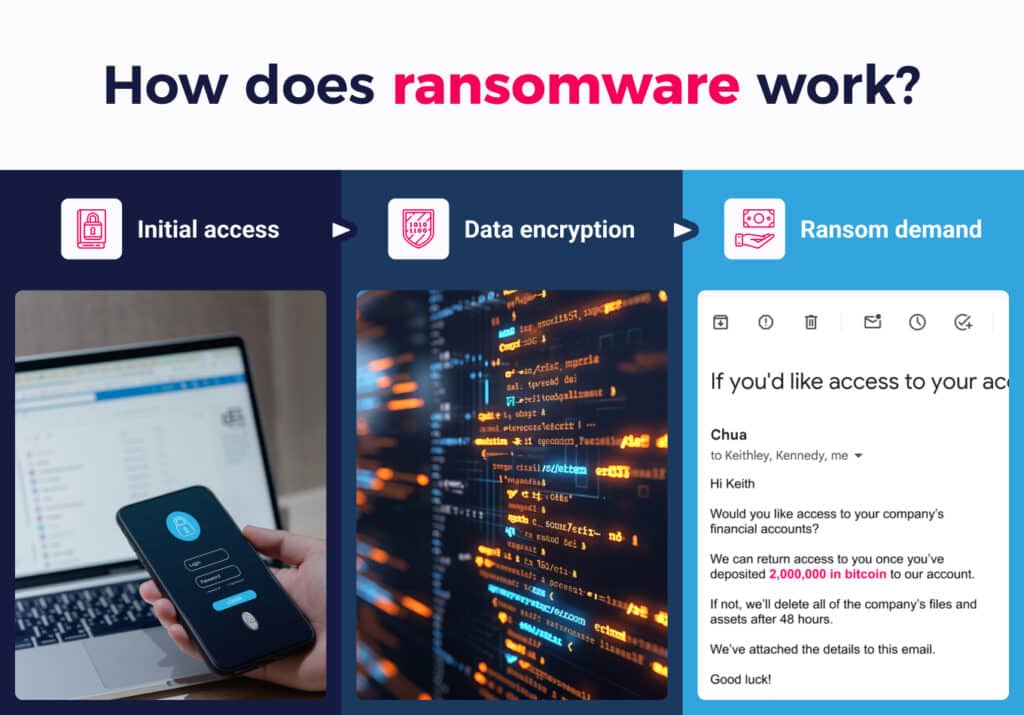
1. Initial access
Ransomware can gain access to your computer system in different ways.
Common entry points:
- Phishing
Phishing is one of the most common entry points for ransomware. A phishing attack is an email that cleverly disguises itself as a legitimate one and tricks you into downloading an infected attachment. In 2023, 69% of ransomware attacks began with a malicious email, so your employees need to know how to tell if an email is from a scammer. - Remote access
Another common entry point for ransomware is remote access technology such as Remote Desktop Protocol (RDP). With the world increasingly moving towards a remote work model, businesses widely use RDP to enable remote working.
Cybercriminals can exploit RDP in multiple ways, including:
- Weak passwords – Cybercriminals use automated tools to carry out brute-force attacks to guess weak passwords and breach your systems.
- Credential theft – Cybercriminals can obtain credentials through various means, such as phishing, or even buy them from the dark web. Once they have valid credentials, they can easily access systems and deploy ransomware.
- Vulnerabilities – RDP vulnerabilities allow cybercriminals to execute code remotely to gain unauthorised access to your systems without the need for valid credentials.
- Weak passwords – Cybercriminals use automated tools to carry out brute-force attacks to guess weak passwords and breach your systems.
- Software vulnerabilities
Unpatched and out-of-date software leaves the door wide open for cybercriminals. They’ll scan your digital infrastructure to identify vulnerabilities, exploit them and create havoc on your systems.
2. Data encryption
Once the ransomware has infected your systems, the software encrypts your data so you can’t access it. The only way to access it again is with a decryption key, leaving you at the mercy of cybercriminals.
3. Ransom demand
Cybercriminals use the encrypted data to force you to pay a ransom demand. The ransom is usually paid in some form of cryptocurrency like Bitcoin, making it more difficult to trace. Upon payment, the cybercriminal will hopefully decrypt your locked files, but there are no guarantees.
Should you pay the ransom?

The official advice is not to pay ransom demands, but it depends on how desperate you are to get the data back. Paying up might seem like a quick solution, but trust us, when dealing with criminals, there’s never an easy way out.
It’s best not to give in to cybercriminals. Here are a few reasons why:
- There’s no guarantee you’ll get your data back
Paying the ransom is a gamble, not a guarantee. Experts report that 92% of those who pay the ransom don’t get all their data back. You’re dealing with criminals, so they’re under no obligation to give back your data. They can easily take the money and run. And, even with the decryption key, it’s unlikely that all the data will be restored with decryption alone. - Increases costs for recovering data
Paying the ransom increases your recovery costs, so you end up paying out more. Figures reveal that businesses that pay the ransom double their recovery costs ($750,000 compared to $375,000 for those who restore their lost data from backups). - Longer recovery times
Paying the ransom can mean longer recovery times. According to the Sophos State of Ransomware 2023 report, 45% of businesses that used backups recovered from an attack within a week, compared to 39% of those that paid the ransom. - You make yourself an easy target
Paying the ransom makes you an easy target, and you’re more likely to be targeted again in the future. A business with a history of paying the ransom is a more attractive target than an unknown target that might not pay up. According to a study by Cybereason, 80% of victims who paid the ransom were hit by subsequent ransomware attacks. - You’re funding criminal activities
If you pay the ransom demand, you’re handing money over to criminals. Obviously, there are moral implications, but you’re also reinforcing the idea that ransomware is a viable business model.
How to prevent ransomware attacks

Ransomware attacks are notoriously disruptive. That doesn’t mean you can’t protect your business.
Here are eight ways to prevent ransomware attacks:
1. Regularly update your software
Your software is only as good as your last patch or update. Unpatched and out-of-date software is plagued with vulnerabilities that cybercriminals can exploit to access your network and systems. Software vendors regularly release updates to fix these vulnerabilities, and neglecting to keep on top of the updates is an open invitation for cybercriminals.
For instance, in 2017, the WannaCry ransomware attack exploited the ‘Eternal Blue’ vulnerability to rapidly spread the infection across old, unpatched versions of Microsoft Windows. It affected over 200,000 computers in over 150 countries, and it even hit the crucial systems of the NHS.
2. Safeguard your credentials
Ransomware attacks, such as the well-known ‘Maze‘ infection, often start with stolen or compromised credentials. It could be the result of a phishing campaign, or they might have exploited known default credentials or used brute force to guess weak passwords.
Here are a few ways to safeguard your credentials:
- Avoid using default credentials
Default usernames and passwords are well-known in the criminal underground, so don’t forget to change them to something more secure.
- Use strong passwords
Make sure you create strong passwords that are more difficult for cybercriminals to crack. Ideally, your password should be 10 or more characters long and contain at least one uppercase letter, number, and symbol. A highly secure password manager such as Dashlane can also protect and manage passwords. - Set up Multi-Factor Authentication (MFA)
Enable Multi-Factor Authentication (MFA) on all access points. This strengthens security by requesting additional information to gain access to your network. It could be a security question, a one-time verification code, or a fingerprint scan.
3. Strengthen email security
Email is a primary route for ransomware attacks, so it’s crucial to have robust email security.
Here are a few ways to improve email security:
- Implement Machine Learning (ML) detection techniques to filter out malicious emails and attachments from untrusted sources.
- Blacklist and whitelist sender email addresses according to predefined rules.
- Use email authentication solutions such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) and Domain Message Authentication Reporting & Conformance (DMARC).
- Provide employees with cyber security awareness training so they know how to spot phishing emails.
For further information on how to improve email security, check out our eight tips.
4. Implement endpoint security
Endpoint security safeguards devices like servers, desktops, laptops, tablets, and smartphones.
Key components of endpoint security include:
- Antivirus and anti-malware software – Detects and quarantines ransomware to protect your devices.
- Application control – Blocks users from installing malicious applications containing ransomware.
- Encryption – Scrambles the data on the endpoint or the full hard disk so it can’t be read.
5. Protect remote access points
Ransomware is increasingly deployed by cybercriminals via vulnerable remote devices and exposed remote services such as RDP.
Here are a few ways you can keep your remote access points secure:
- Use a Virtual Private Network (VPN) for a reliable and secure connection to the internet wherever you are.
- Disable RDP if it’s not needed.
- Enable MFA at all remote access points.
- Install security patches for all known vulnerabilities on your remote access devices and services.
6. Use a zero trust model
Unlike traditional perimeter-focused security models, zero trust acknowledges threats both inside and outside the network. This model enforces strict access controls – distrusting any person or device by default.
Through continuous monitoring and regular re-authentication, zero trust swiftly revokes network access when it detects ransomware. Additionally, the zero trust model adheres to the principle of ‘least privilege’, ensuring that users and devices only have access to the resources they need. This reduces the risk of a ransomware attack and limits the impact of any breach.
7. Network segmentation
Ransomware can spread quickly through a network and bring critical systems to a halt. Network segmentation divides a large network into smaller sub-networks to help minimise the damage. Each subnetwork should have its own unique security protocols, firewalls, and access controls. This slows down the spread of the ransomware and allows you to isolate it before it affects other systems.
8. Back up files and data
Making backups is an effective measure to safeguard your data against potential ransomware attacks. Instead of paying the ransom, you can restore your data from a backup. While backing up doesn’t prevent ransomware, it can help facilitate a faster recovery and avoid costly downtime.
When backing up data, here are some best practices to follow:
- Carry out regular backups of your files, data, systems, and applications.
- Keep your backups separate from your network – either on the cloud or offsite.
- Make multiple backups using different backup solutions and storage locations.
- Make sure devices containing your backups do not permanently connect to your network.
- Protect your backups against cyber threats with robust firewalls, MFA, and encryption.
- Monitor backups and regularly test to ensure everything is working as expected.
- Ensure you regularly patch and update the software you use for backups.
How to recover from a ransomware attack
1. Wipe your devices
Before you restore the data, make sure you wipe the infected devices and reinstall the Operating System (OS).
2. Restore your data and systems to normal
When you’re confident that your devices are free from ransomware, you can restore your data and systems from a backup.
3. Run antivirus software
Once your data is restored, install antivirus software on all your devices and scan the data for infections.
4. Report the attack
If your company falls victim to a ransomware attack, report it to the National Cyber Security Centre (NCSC) and the Action Fraud website. This assists the appropriate authorities in identifying attackers, understanding their target selection, and preventing similar attacks on other businesses.
5. Strengthen cyber security
After a breach, you should re-evaluate your cyber security and strengthen your defences against further attacks. If you don’t have the resources or expertise in-house, you should consider hiring a cyber security specialist like ITVET. We can assist you in establishing a robust cyber security strategy and provide awareness training for your employees.
ITVET can help
With ransomware posing a constant threat to your business, the importance of cyber security can’t be overstated. Despite the financial challenges anticipated in 2024, it’s not the time to take your foot off the pedal. Our team of cyber security experts can help fortify your digital defences to protect your company’s reputation and bottom line. Now you’ve read our Ransomware Guide, the next step is to contact us for a free consultation.